A Configuration Management Database provides you with a 360-degree view of all components of your IT infrastructure. What are the key success factors following the introduction of a CMDB? How do companies benefit from the many possibilities in database and configuration management? What is important for the future? André Jung takes a look at the status quo regarding CMDB.
Content:
- What is a CMDB?
- How does a CMDB work?
- Why do companies need a CMDB?
- Benefits of a CMDB in IT
- Requirements for the modern CMDB
- CMDB in transition: from a technology-centric model to a data-driven strategy
- Conclusion: The CMDB as a source of information for new user groups
What is a CMDB?
A configuration management database, or CMDB in short, is a central database that contains information on all relevant hardware and software components of a company's IT infrastructure. The database allows the IT service to access and manage configuration items (CI). This configuration management refers to items such as servers, computers, telephones, network connections and other network components. A CMDB puts these components in relation to each other and thus shows how interrelationships and dependencies are structured. The CMDB is often referred to as the central element of IT service management and, as a database for configuration management, is an important component of the best practices of the IT Infrastructure Library (ITIL).
How does a CMDB work?
A CMDB permanently exchanges data with other systems and thus obtains information, for example, on the status of various assets. That way, the database can show connections between the individual components. This overarching asset management makes it possible for a CMDB to capture status changes of specific components (e.g., in case of outages, disruptions, or replacements) and analyze in real time the impact on all assets affected by them.
Why do companies need a CMDB?
The use of a CMDB has been standard in modern IT departments for years. Today, no one questions that the CMDB is an important element in asset management. In most companies, the introduction of the systems has cost quite a bit of effort, time and resources. But once the appropriate model has been found and established, the CMDB becomes the cornerstone for customer services, for stable, high-performance and available IT systems and applications, and for a cleanly documented and transparently controllable IT infrastructure.
What are the main effects of the CMDB in IT Service Management?
- The essential support processes, incident and problem management are set up more efficiently thanks to CMDB. Customer satisfaction increases measurably.
- Availability and change management also experience productivity gains. In particular, a graphical representation of the relationships - the interdependencies of service-critical IT components in the CMDB - brings enormous added value.
- The number of fallbacks for change requests and the volume of critical incidents caused by changes are decreasing.
- In many companies, the CMDB now also provides data for asset management.
- The key figures for the availability of IT services at all levels become transparent and improve continuously with the use of the CMDB.
The key to success is the appropriate design of the CMDB model. The relationships of the objects in the CMDB in the context of the service portfolio, their criticality and their dependencies should be the focus. The regular inventory of all elements in the internal IT infrastructure via discovery functions and the template-based integration of external infrastructures enable a realistic image.
Benefits of a CMDB in IT
Implementing a CMDB in the form of a database management system offers companies a number of benefits. These include, for example:
- High agility throughout the entire company
- Central system for all data sets from the IT environment
- Reference point for all assets in IT
- High transparency
- Tracking of the development of IT assets even in complex infrastructures
- Overview of irregularities and based on that quick maintenance and troubleshooting
- Simple integration of external data through interfaces
In addition to the IT department, the entire company benefits from the improved processes. However, the requirements for such a system are constantly becoming more complex. So what exactly does a modern CMDB solution need to look like in order to address current topics and issues?
Requirements for the modern CMDB
One development that is steadily influencing the overall strategic direction of digital transformation, service architecture, and thus inevitably IT management systems including the CMS, is the question of the security, protection, and integrity of all data, information, and services used in the enterprise. The following aspects are particularly relevant:
Digital security and data protection
The number of attacks on corporate IT has constantly been increasing in recent years. The damage to the business and public perception of the affected companies is increasing as well. This has led to a shift in priorities: In order to ensure the compliance of the entire company, questions of security and data protection are strategically very high on the agenda. And a first-class security concept is the basis for digital transformation.Avoiding errors and security gaps
Foresight and the ability to plan can help avoid expensive missteps and dangerous security gaps on the path to digital transformation. To do this, IT needs a comprehensive, deep understanding of the data and information and how they are linked in the central CMDB.Future-oriented security management
The CMDB can fulfill an important new role by providing the data that supports predictive security management. The focus of the CMDB is thus no longer on mapping purely technical configuration items (CIs) and their attributes. Instead, meta-information of a different kind is to be obtained from the CMDB.Relevant issues in companies - the CMDB as a prediction platform
- When are migrations to more recent versions due and what are the costs involved?
- Are outdated versions of firmware, operating systems, applications or interfaces already being used in your own infrastructure or in virtually integrated cloud services?
- How do you identify and assess risk scenarios arising from outdated software and known or newly discovered vulnerabilities?
- Does internal patch management conform to that of partners and service providers with whom integrations and cross-enterprise workflows exist?
- Which applications can be streamlined or replaced with better alternatives?
- At what point should business critical applications no longer be supported?
- How do applications support critical business services, such as customer relationship management (CRM), production control and maintenance planning, or ERP, and what effects can be expected when these applications or their IoT sensing are migrated to the cloud?
- What insights and decision support can be gained from modeling new applications and business services?
- What data-based dependencies exist between business-critical applications and how do inconsistent or corruptly transferred data sets impact business capability?
The effort to answer these important questions using established management systems - including the traditional CMDB - is enormous today. One way to find answers is to evolve the CMDB into a prediction platform that not only serves the status quo, but also supports modeling of future architectures and migration paths while generating risk predictions for alternative courses of action.
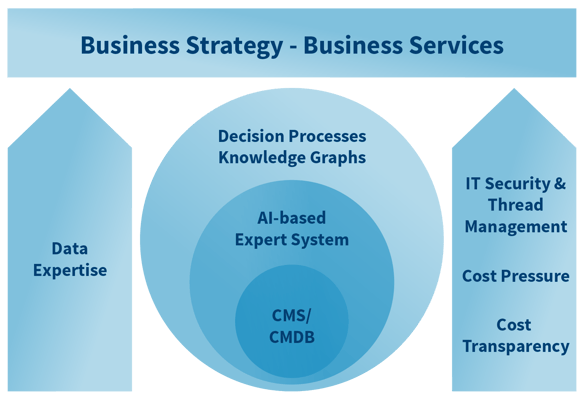
Image: The CMDB as the core of a strategic data & analytics framework for ITSM
CMDB in transition: from a technology-centric model to a data-driven strategy
The goal of a platform for data-driven decisions presents IT with the classic task of extracting information from data and generating knowledge and insights from information. The pillars on this path are the mapping of the essential data sources in a meaningful context to the processes, the IT services and to the business services. The view covers all levels of the infrastructure – from the firmware of the network switches to the server platforms to the APIs of the cloud services, their configuration, performance and degree of utilization.
The aim is to create a new, abstract, but reproducible and verifiable level of knowledge. A goal that, on the one hand, requires the already mature and always up-to-date CMDB, and, on the other hand, can be achieved with the help of an AI-supported expert system. This requirement should not be underestimated, especially because success cannot be achieved with technical changes alone.
New questions arise for IT managers
The change in database management systems brings up new questions for those responsible in IT:
- Where are the Configuration Management System (CMS) and the CMDB headed?
- What future benefits can be generated in practice beyond the added value already achieved?
- Which strategic processes, such as IT security management and business service management, can benefit from the central CMDB?
Two drivers in particular come to the fore here: IT financial management and security management. On the support process side, sustainable increases in quality and efficiency can be demonstrated, but cost reductions cannot be clearly identified. Today, cost pressure is driving many innovations and demands transparent service costs both for the provision of internal services and for the increasingly used external infrastructure services. At the top of the list are the various cloud services for applications, infrastructure and IT security services.
Relevant components for the successful implementation of transformation within the company
- the development of a data and analysis strategy based on the CMDB and other data and information sources
- the introduction of a data and information management program as an expert system with knowledge graphs that help prepare complex decision-making processes and visualize resilient fundamentals
Last but not least, a data-driven culture should be established in the company, fostered for example by a new leadership position: The Chief Data Officer (CDO). This provides an environment in which all stakeholders contribute to the overall picture and work together to master the transition from a technology-centric to a data-driven strategy.
Conclusion: The CMDB as a source of information for new user groups
The new role of the CMDB expands the typical user group. Whereas up to now it has been people like service desk agents, change and release managers, problem managers, process owners, auditors, etc. who work in and with the support processes, it will soon include colleagues who are responsible for business services and their further development.
These include:
- Enterprise and service strategy & architecture teams
- Business service management
- Financial management
- Purchasing and supply chain and vendor management
- IT security teams
- And – with new objectives – the IT service and operations teams.
These groups can leverage the enhanced CMS for a business strategy informed by data & analytics.
Serviceware experts help you take your IT services to the next level with the help of a modern CMDB to optimize enterprise-wide operations.

 German
German

